I archived my “Projects” page as it’s getting on in years since I have last worked on one outside of… Read more Past Software Projects
How I Got Started In Crypto
“Think about the most important thing you could be working on right now… Why aren’t you working on that right… Read more How I Got Started In Crypto

Twitter Thread on Rare Pepe NFTs
Original Tweet thread 6.5 $BTC for this NFT? And that’s a “low-ball?” Might seem strange for the uninitiated, but this… Read more Twitter Thread on Rare Pepe NFTs
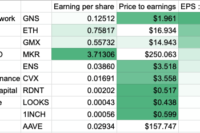
Twitter Thread on Protocols with “Real Yield”
Analysis of some tokens that are earning revenue
Crypto Twitter Threads
A running list of Twitter threads about crypto

Twitter Thread on Tezos Baking Ecosystem from 2020
An update on the Tezos Baking ecoystem

Twitter Thread on Tezos from 2019
Overview of Tezos baking and its growing ecosystem
Examples Where You NEED Crypto
I constantly see examples where you need a blockchain to achieve some completely new behavior and solve problems in interesting… Read more Examples Where You NEED Crypto
Ethereum Whitepaper
Just like the Bitcoin whitepaper, I am hosting the Ethereum whitepaper (mirror) on my site to keep more copies on… Read more Ethereum Whitepaper

Bitcoin Whitepaper
I am hosting a copy of the Bitcoin whitepaper (mirror, backup) on my website in an effort to create more… Read more Bitcoin Whitepaper
Dominant Strategies
The history of mixed martial arts (MMA) is an example of how dominant strategies emerge in adversarial environments. An adversarial… Read more Dominant Strategies
Butterfly Effect
I think people discount the butterfly effect. One small event sets in motion a series of events that create large… Read more Butterfly Effect
Crypto Use Cases
But what’s the use case? Where are the use cases? The use case? Use case?Here ya go:
Proof of Stake and Proof of Work
Proof of work has proven effective ever since the network was launched just over 10 years ago. Complex systems are… Read more Proof of Stake and Proof of Work
How Bitcoin Dies (Maybe, Hopefully Not)
Let’s hope this post doesn’t age well. Recently, there was a bug in Bitcoin (arcanely called CVE-2018-17144) that could have… Read more How Bitcoin Dies (Maybe, Hopefully Not)
The Real Satoshis
In this post I will chronicle evidence on the real identity of Satoshi Nakamoto that I have stumbled upon over… Read more The Real Satoshis
A case for using Tor
If you care about privacy, I advocate downloading The Tor Browser. Tor is a private web browser. It’s like Incognito… Read more A case for using Tor